Adopted on 27 April 2016, the General Data Protection Regulation (GDPR) will replace the 1995 Data Protection Directive 95/46/EC, taking force on 25 May 2018. Thus, the European Parliament, the Council of the European Union, and the European Commission are aiming at creating Digital Single Market. The forthcoming GDPR is expected to influence particularly those who work with personal data.
The GDPR imposes heightened requirements on controllers, i.e. organizations that control the processing of personal data, encouraging them to implement protective measures. When some organization wants another vendor to take on any or all its responsibilities, a need to transfer personal data to this outsourcing vendor arises. Nevertheless, the organization remains the controller even upon transferring the data and shall be liable for data protection breach.
Personal data and pseudonymization
Since the Regulations will in the first place affect the personal data protecting and processing policy, it is important to understand what this term implies. According to Article 4(5) of the GDPR, the term “personal data” is applicable to any information about identified or identifiable living individuals, such as a name and surname, a home address and an email address (e.g. [email protected]), location data, an ID number, or an IP address.
Besides, the Article clarifies the ambiguity surrounding the concept of pseudonymization, essential for a better understanding of the subject. As stated in the GDPR, pseudonymization refers to the processing of data so that to ensure that they cannot be attributed to a specific individual. To put it another way, pseudonymization prevents the attribution of the data to a natural person. As a useful security measure, it reduces the risks of direct identification under the GDPR.
Under the new act, both automated personal data and manual data are subject to protection. It means that no matter whether data are collected automatically from existing services or added manually with the restricted accessibility to them according to certain criteria, they fall under the new Regulation.
Practical effect
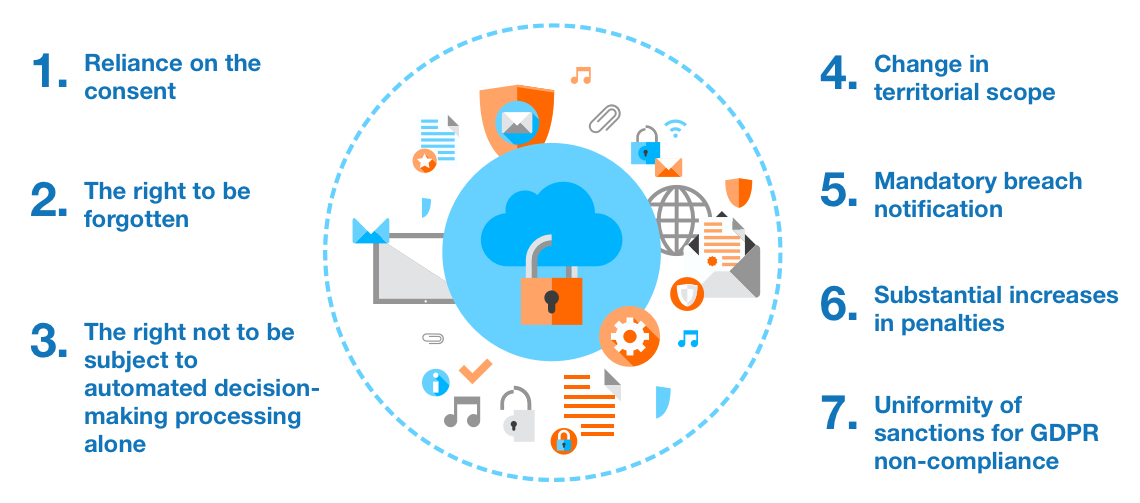
Strictly speaking, the GDPR is the first uniform breach notification law. This Regulation will be applied when the risk to the rights and freedoms of the data subjects occurs. However, when it takes effect, individuals will have to keep in mind the following changes:
1. Reliance on the consent
The right to have personal data deleted outweighs your right to process what you have obtained from the individuals. This is one of the trickiest parts. Transparency and accountability are the issues here. Therefore, data holders upon gaining consent will have to document it demonstrating what they do with the information received.
2. The right to be forgotten
Thus, individuals will be able to request the erasure of their data. As it was stated above, the interest of an individual outweighs the interest of a responsible body. It means that the request to correct, delete or block certain data must be complied with, regardless of whether this information has been saved lawfully or not.
3. The right not to be subject to automated decision-making processing alone
These are five core safeguards to be applied as a framework to protect data subject’s rights:
- Transparency as a way for a data controller to inform a data subject in advance about using his or her data for making automated decisions.
- Participation, which allows a data subject to express his or her opinion on the upcoming decisions.
- Internal oversight as prior confirmation or validation by a human expert the real-time outcomes once the automated decision is needed. Tools using machine learning can sometimes undertake this task, although for a higher accuracy human monitoring is recommended.
- External oversight as posterior evaluation conducted by external supervision authorities.
- Traceability, which is vital for external supervision in terms of the transparency of both processes and outcomes.
4. Change in territorial scope
The GDPR does not exclude international organizations (IOs) as bodies set up by an agreement between two or more states from its scope. It implies that data privacy is bound to be protected for all EU citizens, yet it does not depend on the location of the company. In fact, EU data protection laws often extend territorially having effects outside the boundaries of the EU legal order. In the case of the new Regulation specifically, Article 3(1) states that the GDPR applies to processing data regardless of whether an IO has an EU establishment or not. What matters is the offering of goods and services to data subjects within the European Union, and the monitoring of these subjects’ activity as far as it concerns EU individuals.
5. Mandatory breach notification
This presupposes that data protection authorities are to be informed about a personal data breach within 72 hours of its discovery.
6. Substantial increases in penalties
Non-compliance will thus be liable to administrative fines up to 10 (20) million euros, or up to 2% (4%) of the total annual turnover depending on the type of the infringement.
7. Uniformity of sanctions for GDPR non-compliance

What does the GDPR mean for software development?
The new Data Protection Regulation is meant not only to create a better legal structure but also to protect users from software abuse. Thus, the GDPR will carry out this function by covering any company that is processing personal data of subjects residing in the EU. The company’s location and the location where the processing occurs are of no importance.
Most of the enterprises providing IT services require personal information of their customers to perform necessary business processes. Therefore, any fault to protect data being collected, stored and shared all over the world can negatively affect the data subjects and undermine the enterprise’s reputation.
With the enforcement of the GDPR, the implementation of specific aspects related to privacy by design (PbD) will become mandatory for many companies. It can promote privacy, for the IT systems will have to focus on supporting the principles relating to the processing of personal data. On PbD conditions, legal requirements and customers’ privacy preferences should be analyzed and improved by integrating privacy enhancing technologies (PETs.) However, PbD comprises much more than a mere implementation of a few PETs.
Why take risks?
Even though privacy and security risks exist, pursuing innovation through data analytics is not what organizations should fear. Instead, it enables them to capitalize on the transformative potential of Big Data by safeguarding personal information. This central motivation for PbD fits the EU General Data Protection Regulation perfectly since PbD is in the first place aiming at preventing privacy violations from arising. Therefore, outsourcing vendors as third parties to whom data are disclosed should consider the changes introduced by the new EU Regulation and all possible data protection safeguards to establish user trust and gain public acceptance of their technologies.

© 2018, Vilmate LLC




