Using biometrics for authentication, access control, and fraud prevention can hardly be considered unique or extraordinary nowadays. Moreover, tracing back the history of biometrics, one can conclude that such systems, which used unique biological characteristics to authenticate the identity of a person, might be dated as early as 500BC. Those were the most primitive forms, but that also was the starting point from which they have been continually evolving to finally enter the biometric boom era during the second half of the 20th century.
Biometric measurements also have developed from fingerprinting to make up a wide variety of forms of non-contact biometric identification systems. Now, they are particularly quickly growing in popularity due to the global pandemic. It’s for health and safety reasons, there emerged an urgent demand for biometric identification through contactless sensors. In order to adapt successfully to the new normal, it is essential to understand how much better the non-contact form is and how to apply it properly in the context of the pandemic crisis.
What is biometric identification?
So, what is biometrics? Biometrics identification is a safe and secure identification method that uses the unique physical characteristics of an individual for automated recognition. In 2013, Apple included fingerprint to unlock the newly launched iPhone 5S, thus beginning the widespread utilization of biometrics as a means of user authentication. The technology is already used around the world so that it is increasingly replacing typical passwords and access keys. Even the Asia Pacific region is expected to be witnessing robust growth and the subsequent commercialization of the biometrics industry resulting from government initiatives such as India’s Aadhaar or CRIC (China Resident Identity Card.)
The global biometrics market is forecast to reach $45.96 billion by 2024 as the network formed by partnerships between tech, and biometric companies will be expanding. The range of solution portfolios is also going to grow bigger to include and retain such biometric data as fingerprint, face, iris, vein, voice, DNA, palm prints, hand geometry, signature, and a number of behavioral features.
It all sounds like biometrics is super practica,l and there will no longer be a need for people to come up with those endless unique letter-number-special-character password combinations for each new account. So, biometric identification is convenient, but does it ensure biometric authentication security and the safety of personal data?
As the biometrics definition goes, such systems can recognize a person’s specific physical attributes, their fingerprints, facial features, iris, retina, and more. And companies using biometric information have to ensure that biometric data is always securely stored and encrypted. Ideally, it must be done on end-user devices and not in some remote cloud storage. This potentially makes it harder for hackers to get to users’ private information, but unfortunately, that is not always adequately taken care of. The technology used in biometrics varies in the level of complexity. So, the more elaborate the technology, the higher the level of security.
Types of biometrics: physiological and behavioral
Biometric sensors or access control systems that are often used for security can be labeled into two major groups, such as Physiological Biometrics and Behavioral Biometrics. Essentially, they differ in types of biometric sensors involved and biometric input being processed.
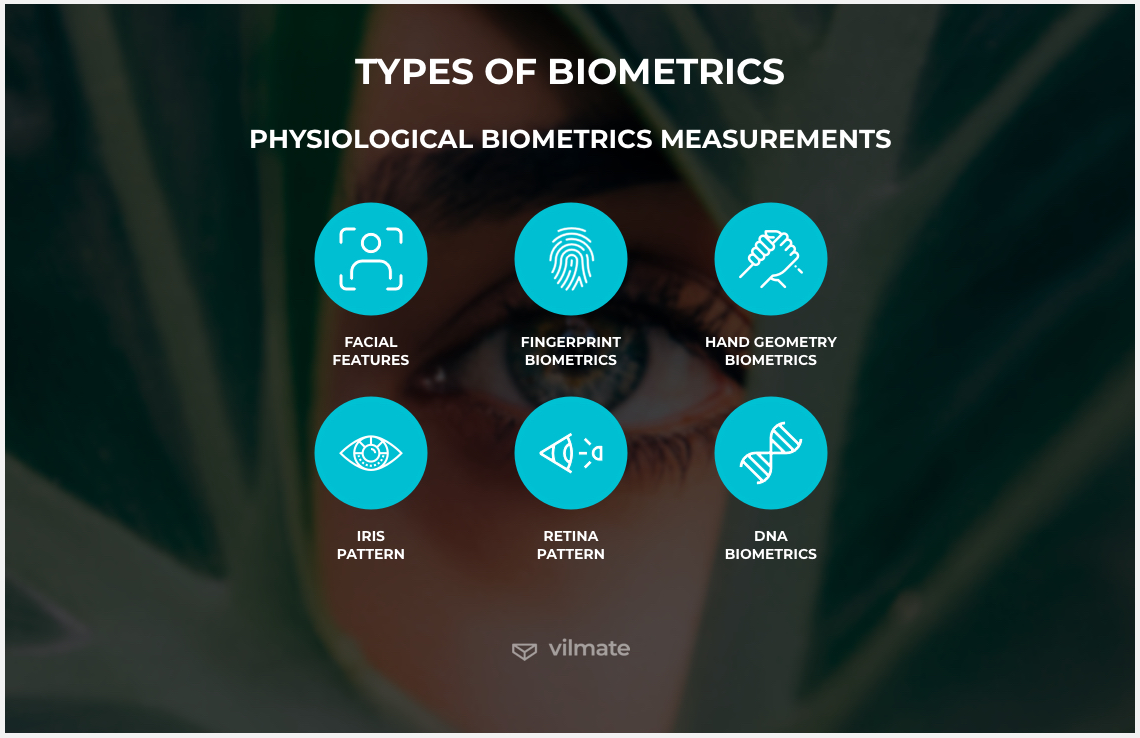
Physiological biometrics measurements
For a quick physiological biometrics definition, physiological biometrics are biological measurements that use the structure of a human body and its genetic- or molecular-level traits (DNA and blood) to identify a person.
As one of the oldest and most popular physiological biometric measurements, fingerprint biometric authentication is obviously far more convenient than using a password to log in. One just puts their finger on the reader or identifier, and then they’re immediately admitted in, that’s much faster and easier than manually typing a password. Besides, the passwords are often weak and hackable. This method is gradually becoming outdated, but password-protected systems are still the easiest to implement. That’s probably why they’re so common. Other physiological biometric measurements include:
- Facial features
- Fingerprint biometrics
- Hand geometry biometrics
- Iris pattern
- Retina pattern
- DNA biometrics
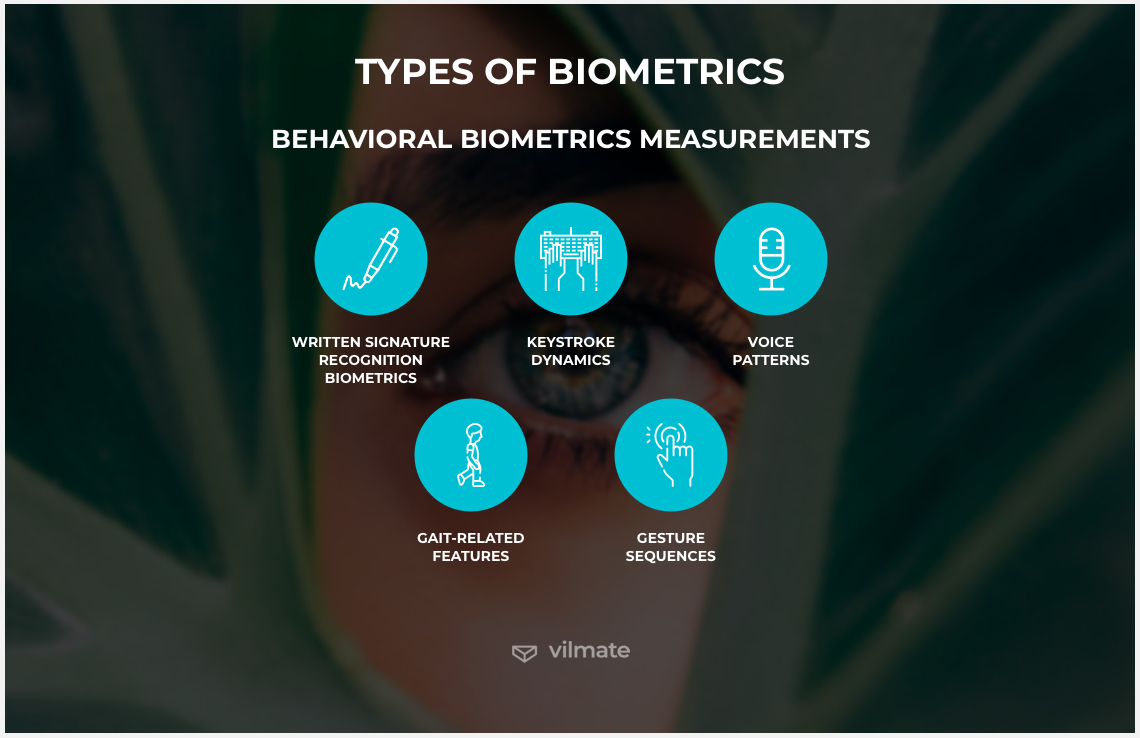
Behavioral biometrics measurements
Behavioral biometrics is an alternative option for identifying a person by the physiological measurements. There, smartphones and wearables analyze behavioral attributes like, for example, the way we type or talk. Simple behavioral sequences such as how one gets their smartphone out of the pocket can be enough for a system to identify who the person is.
Linking this technology to the movements that we all make day by day can be very convenient as it eliminates the necessity to do anything special to authenticate oneself – the software will tap into our smartphones and wearables sensors to do the job. Then, the trust level gets calculated based on the user’s behavior. This means it assesses the odds that the person under consideration is really the owner of the device and not some stranger.
The advantage of this behavioral system is that the third party doesn’t actually have to save each movement profile. The data is only registered by the user’s smartphone. Then, the trust score is calculated there. No actual sensitive private information is shared with a service provider or saved on a cloud, only this score gets disclosed. That makes the behavioral biometrics-based method particularly secure. Its introduction to a broader audience would put an end to a big security problem that we currently have. The leaked password files and leaked biometrical data won’t be an issue anymore. By using behavioral profiles, this problem would disappear in no time.
Behavioral security and multi-factor authentication are very secure. As a rule of thumb, the more elaborate the security method in sensors, the better. History of behavioral biometrics goes back to the 19th century. Having started with the invention of the telegraph, it got adjusted to the new technological developments that are now represented by behavioral measurements like:
- Written signature recognition biometrics
- Keystroke dynamics
- Voice patterns
- Gait-related features
- Gesture sequences
Advantages of contactless biometric authentication
A password can be stolen. A stranger can watch you enter it somewhere or find it where you wrote it down or even just guess it. This wouldn’t happen with biometric identification technology. Besides being convenient and saving users from having to remember passwords, biometric authentication has other advantages to offer to people. And these advantages revolve around the qualities of human features this authentication method relies upon.
Regardless of what the biometrics technique we consider and what is a biometric system used for, they all have in common that they all collect human characteristics which are:
- Distinctive - they enable differentiation by individual traits and patterns
- Universal - all people possess or express them
- Measurable - they can be measured for the sake of future comparison
- Persistent - collected in a reliable manner, they are either permanent or temporally invariant
- Recordable - if given consent to, they are recorded by the biometric verification reader
- Forgery-proof - biometrics uses characteristics that cannot be forged using fraudulent methods
Biometrics trends: non-contact identification
Up until today, there is no optimal biometric measurement that would perfectly satisfy all of the operational requirements. However, it is fair to claim that in 2022, amid a pandemic, the non-contact or contactless methods of biometric-based identification lead the industry.
Fingerprints have long been a primary technique for biometrics identification. The security of smartphones, laptops, and other smart devices has literally been at one’s fingertips. The pandemic, of course, made its allowances, and fingerprint biometrics, in which sensors require tight contact with a finger, is although secure for one’s data, not that safe for the person’s health anymore.
Fortunately, a whole bunch of contactless biometric scanning methods had been successfully researched yet before the crisis, so that today, there is a rich selection of alternative contactless solutions available on the market.

1. Facial recognition. This form of biometric authentication has proven to be one of the most intuitive means of non-contact biometric identification. The face recognition system does not need a close person-to-machine contact to do its job well. And the algorithms that enable facial recognition are getting ever more accurate due to the power of Artificial Intelligence. Under excellent conditions, facial recognition systems can have near-perfect accuracy. The study of facial recognition accuracy claims that it can be as high as 99.97%.
However, that brings up a cost issue. The more senses one can use to scan a face, the more accurately one can capture someone’s biometric profile. In a similar vein, the security of this technology depends on how well it’s implemented. If there’re more sensors, this will be more secure than passwords.
2. Iris identification scanner. Iris recognition is similar to fingerprints scans and facial recognition in the way that they’re all checked for a single constant biometric feature, by which the system recognizes a particular human being. A password, by contrast, is something one needs to memorize. One shouldn’t write it down anywhere because otherwise, anyone who finds it can pretend to be that person. The future is in multifactor or at least two-factor authentication. And the iris has the potential to become one of those factors.
The structure of an iris is singular to every individual, and even identical twins whose eyes are indistinguishable, too, do not share the same iris pattern. Irises are essentially a lot like fingerprints but are also more complex and difficult to hack. Iris-recognition systems normally convert every pattern into a binary code for the software to then quickly match between that code and those other codes stored in a database. Currently, there is enough optimism to believe that commercial iris recognition will improve to such an extent that they will be able to meet future security challenges.
3. Ear identification. Ear biometrics uses ear print and earlobe geometry analysis to identify a person. Similar to facial recognition, biometrics that is based on ear features can be used in passive identification, meaning that no actions are required from an individual. Therefore, they can unobtrusively authenticate themselves. Ear geometry is unique to each human. Modeled as a graph from the side-face image, ear biometrics is also robust and easily extractable, which is similar to fingerprinting. Importantly, each individual’s ear presents a more stable than facial features source of biometric data, as it is less affected by users’ emotions and ages.
The human ear can be subject to non-contact authentication, but the use of this method is currently limited due to the complexity of data collection and analysis processes. It’s plain to see that ultimately, the most user-friendly systems will be the ones used the most. That is not yet the case with ear identification, but the method has the potential to become more widely applicable if the subject is further researched and improvements are made.
4. Gait identification. To get access to some high-security area, a computer first needs to scan the body movements of a person. There is software that captures how fast we walk, the length of our steps, and our hip movement and uses this data to create a movement profile, by which it authenticates us. The smartphone can then communicate with a gate, for example, and unlock it when we approach. But if one’s movement doesn’t match the profile, the door will remain locked.
In recent decades, a person’s gait has developed into a reliable behavioral biometric trait. It has the benefit of being trackable at a distance and is nearly impossible to impersonate. Gait recognition relies on different modalities (sensor- and vision-based), which noticeably boosts the success and accuracy of the model. All in all, these recognition systems today involve a significant scope of research, and the interest in studying this method of authentication keeps increasing.
5. Hand vein capturing. Not only biometric fingerprinting but also palm or finger vein capturing is popular nowadays, especially in banking and financial applications. These systems look under the person’s skin, so to speak, and use infrared scanners for vein matching. Oxygen-poor blood in veins absorbs more infrared light than surrounding tissue so that vein patterns can be matched.
Hand veins are privacy-focused biometrics. Unlike fingerprints, vein geometry is nearly impossible to mock, and it cannot be stolen. Besides, it is one hundred percent contactless. Using a non-contact burst of infrared light, the technology maps internal vein structure, so there is no need to touch any sensors. For these and some more reasons, the vein biometrics market is forecast to generate over $1B annually by 2029, led by banking, financial services, and insurance.
6. Voice recognition. Voice ID can be a new security enhancement that makes it easier, faster, and safer to verify your identity. Checking voice biometrics can effectively serve as a second layer of the two- or multi-factor authentication. Today’s smartphones are generally suitable for recording a person’s voice for security-check. It can be, for example, a text-dependent algorithm that will use different phrases for user enrollment and recognition. Another method is to request a user to come up with a set of unique phrases and ask them to say one of those phrases out loud for their identity verification.
Each user has to be able to train the in-built voice recognition system by making several records of the same phrase. Then, the system’s recognition ability will improve, and it will be able to work for people in face masks or even biosafety suits.
Non-contact biometric identification systems will witness a broader use in the nearest future. And the diversity of biometrical data that can be used for identification purposes promises much more convenient and secure experiences for users.
In this regard, many can wonder if the convenience outweighs the potential risks. Researchers are already working on so-called cancelable biometrics that will allow handling the issue of hacked biometrical data, which, unlike passwords, cannot be changed. Here the biometric data is encrypted before it’s stored. In a nutshell, this means that not one’s actual face is stored but a digitally altered version. If anyone hacks the system, one can delete their data and create a new biometric password.
Conclusion
Contactless biometric verification that enables user authorization without a human touching any machine sensors is a hot topic. Moreover, behavioral security technology and multi-factor authentication relying on non-contact biometrics are far more secure than the methods that we are used to. They have become a big point of attention to researchers in recent decades, and the interest continues to increase in light of recent events. This means there is a probability that contactless biometric systems will grow even more elaborate, and powered by better sensors, they will provide safer applications.
So, there is a lot to look out for to be in sync about the latest trends and developments in biometrics authentication technology. And we believe it will always be important for software providers to ensure convenience and security to people in the most up-to-date way.

© 2022, Vilmate LLC